Surely you have heard the word more than once, and we are sure that you probably know what it is, but Phishing is becoming a bigger problem on the net today.
Remember that phishing is the act of trying to trick the recipient of a malicious email into opening it and following its instructions. The “sender” of the email tricks the victim into making the message appear to come from a trusted source, such as a state agency, supplier, or company customer.
We will show you 5 types of phishing that will help you detect them more quickly:
1.- Traditional Phishing
This type of attack is the simplest when is technically analyzed; it´s normally linked to a copy of a site known to the victim, in which the address where the entered data arrives is changed. In this way, the cyber criminal steals the credentials entered by the victim, which can be housed in plain text in, a text file or sent to an email box.
In the following image, we can see a phishing site that affects Paypal, which has been mounted on another allegedly violated, which was then used to create the fraudulent site.
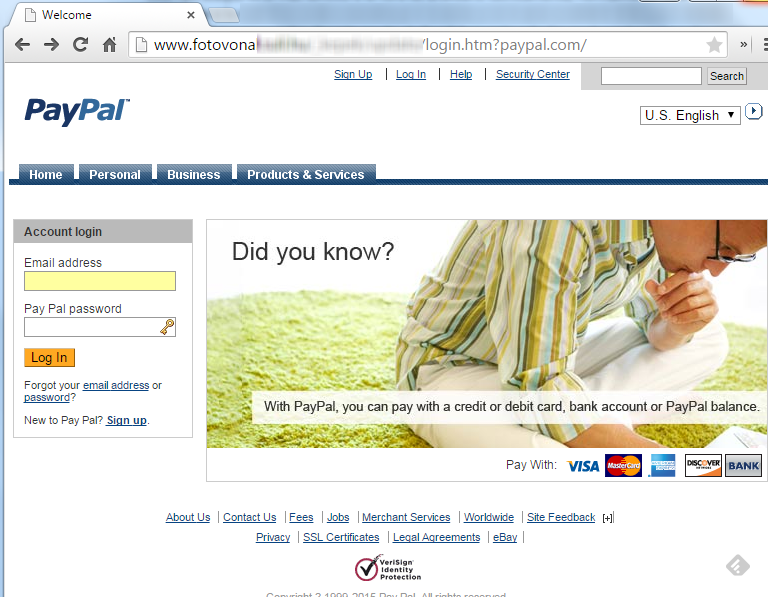
2.- Phishing Redirector
It is a mass mailing and it does not have a specific recipient. It is widely used to obtain bank details.
This procedure has a higher level of complexity and unlike the previous one, it uses at least two or more sites or domains to perpetuate the scam. There are several ways known and that can be classified within this type of phishing.
3.- Spear Phishing
This class has as its main difference that it is aimed at individuals or small groups. In this way the campaigns are much more personified and with a higher percentage of victims.
Rarely do they see cases that affect banks or social networks, because they do not seek massiveness but quite the opposite; in fact, this type of method is used in attacks such as APTs, targeting company employees with specific profiles. This means that victims could receive personified emails with first and last names, even falsifying known addresses to generate greater empathy and trust from a unwary navigator.
4.- Smishing SMS
Text messages are sent alerting the victim that he has won an award. The victim must respond with some type of code or special number to validate their false prize.
Now you will wonder after seeing this that it is inevitable to receive messages that may be phishing, but by following some steps we can manage not to fall for the scam.
Offer training to the weakest link. Phishing requires a user to open or click on something malicious. Therefore, it is vitally important to train employees so that they know how to recognize, avoid and report different types of phishing.
Implement multiple layers of security defenses. Based on the principle that cybercriminals will do everything in their power to avoid your security methods and that they will change their tactics, it is best to follow an in-depth defense security strategy. Start with an email filter that scans all incoming emails; this way, it will intercept a good part of the phishing attempts. Then use an endpoint antivirus product that includes phishing protection. Lastly, implement a solution that examines the outgoing web request if a user clicks on a malicious link. This solution can be based on DNS or proxy.
Turn on multi-factor authentication. Even taking all of the above precautions, there is a chance that you will experience a phishing attack and the cybercriminal will steal an employee’s username and password. To mitigate this risk, implement multi-factor authentication. This will ensure that even if your credentials are stolen, malicious agents cannot access your company’s applications, services, or confidential information.

